Role of Internal Audit in Cybersecurity Compliance
- Леонид Ложкарев
- 2 days ago
- 8 min read

Cybersecurity threats challenge organizations in the United States at every turn, creating high stakes for chief audit executives and internal auditors responsible for safeguarding financial and compliance operations. Strong cybersecurity frameworks like the NIST Cybersecurity Framework and CISA standards offer flexible pathways for addressing risk and aligning controls with business priorities. This overview delivers practical insight on building robust audit practices, connecting technical security, governance, risk assessment, and regulatory compliance to drive measurable improvements and strengthen protection.
Table of Contents
Key Takeaways
Point | Details |
Proactive Risk Management | Internal auditors must anticipate cyber threats by leveraging technical knowledge and strategic insights to enhance organizational security. |
Comprehensive Risk Assessment | A robust risk assessment process involves identification, quantification, prioritization, and continuous monitoring of vulnerabilities. |
Integrated Cybersecurity Frameworks | Auditors should utilize multiple cybersecurity frameworks to create a holistic understanding of risks and support organizational compliance. |
Effective Cybersecurity Governance | Governance requires active board engagement and integration of cybersecurity into enterprise risk management to drive strategic oversight. |
Core Concepts of Internal Audit in Cybersecurity
Cybersecurity compliance represents a critical battleground for modern organizations, where internal audit functions serve as strategic defenders against evolving digital risks. Internal audit standards provide the essential framework for protecting organizational digital assets through systematic assessment and risk management.
At its core, internal audit in cybersecurity involves a comprehensive approach to evaluating and enhancing an organization’s digital security posture. Key responsibilities include:
Assessing current cybersecurity infrastructure and protocols
Identifying potential vulnerabilities and compliance gaps
Developing strategic recommendations for security improvements
Ensuring alignment with industry regulatory requirements
Validating the effectiveness of existing security controls
The strategic role of internal audit extends beyond mere compliance checking. Auditors must function as proactive risk managers, leveraging deep technical knowledge and strategic insight to anticipate potential cyber threats before they materialize. This requires a holistic understanding of technological ecosystems, regulatory landscapes, and organizational risk tolerances.
Modern internal audit teams must blend technical expertise with strategic thinking. They need capabilities that span technical security assessment, regulatory compliance understanding, and organizational risk communication. Successful cybersecurity auditors combine technical skills with strong analytical capabilities, enabling them to translate complex technical findings into actionable business recommendations.
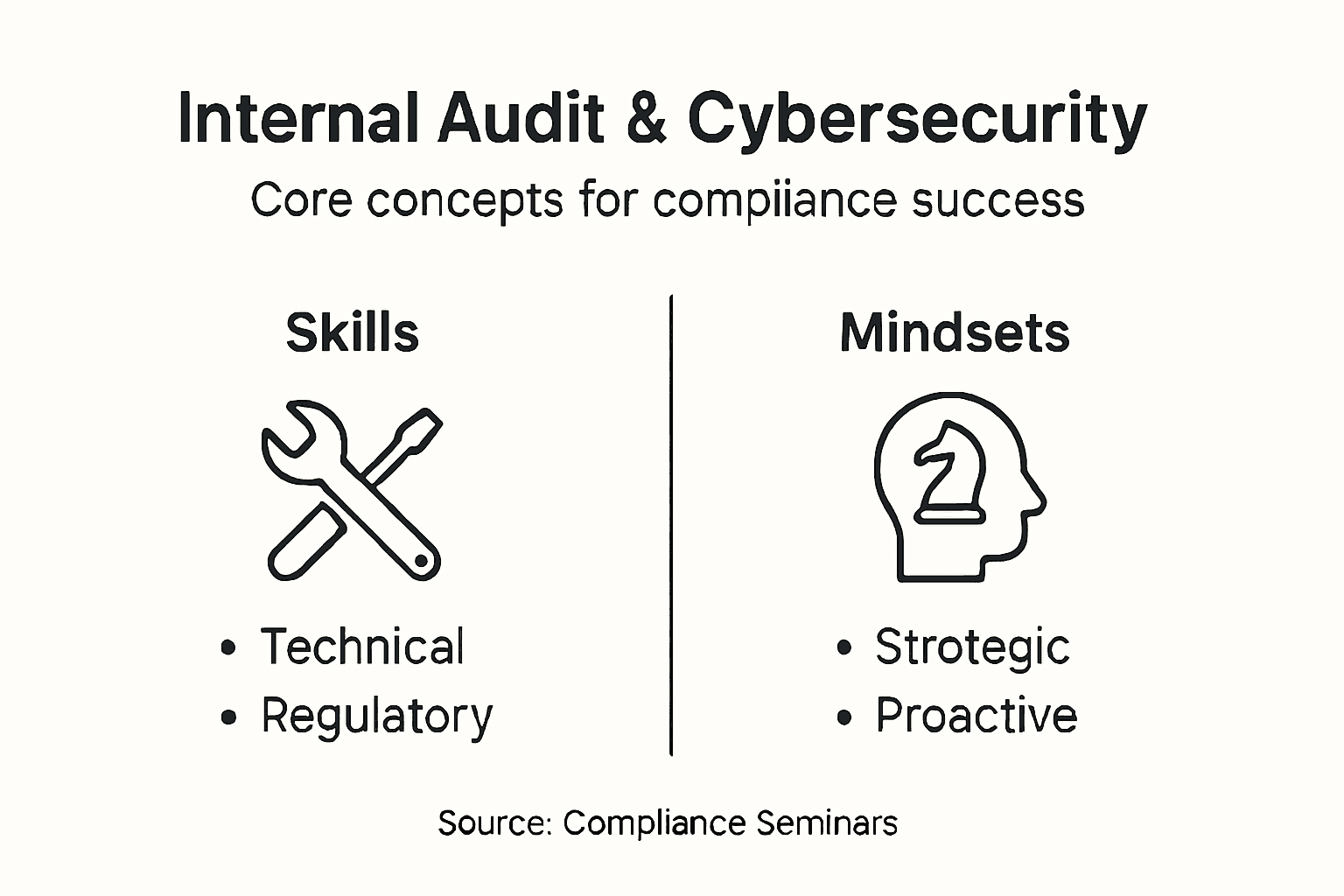
Pro tip: Develop a comprehensive cybersecurity skills matrix that maps technical competencies, regulatory knowledge, and communication abilities to create a robust internal audit function.
Cybersecurity Frameworks Used by Auditors
Cybersecurity frameworks serve as critical navigation tools for internal auditors, providing structured approaches to assessing and managing digital security risks. NIST Cybersecurity Framework represents a foundational methodology that enables organizations to comprehensively evaluate their cybersecurity posture across multiple dimensions.
Key cybersecurity frameworks that internal auditors frequently utilize include:
NIST Cybersecurity Framework (CSF): A flexible, risk-based approach for managing cybersecurity risks
CISA Critical Infrastructure Cybersecurity Framework: Focused on protecting essential organizational systems
ISO 27001: An international standard for information security management
COBIT: A governance framework for enterprise IT management
SOC 2: A framework for evaluating security controls in service organizations
The strategic implementation of these frameworks requires auditors to move beyond checklist compliance and develop a nuanced understanding of organizational risk landscapes. Each framework offers unique perspectives on cybersecurity governance, with auditors selecting and combining approaches based on specific organizational needs and industry requirements.
Here’s a comparison of popular cybersecurity frameworks auditors use and their primary focus:
Framework | Core Purpose | Industry Usage |
NIST CSF | Risk management and response | Broad, especially critical infrastructure |
ISO 27001 | Information security management | Global, all industries |
SOC 2 | Controls for service organizations | Tech, SaaS, service firms |
COBIT | IT governance and management | Large enterprises, IT-focused sectors |
CISA Framework | Securing essential systems | U.S. government, critical sectors |
Successful cybersecurity auditing demands a comprehensive approach that integrates multiple frameworks. Auditors must understand not just the technical controls, but also the strategic implications of cybersecurity risks. This involves translating complex technical assessments into meaningful business insights that can drive organizational security strategy and risk mitigation efforts.
Pro tip: Develop cross-framework competency by creating a comparative matrix that maps control objectives across different cybersecurity standards to enhance your audit effectiveness.
Internal Audit’s Risk Assessment Process
Risk assessment represents a cornerstone of effective internal audit practices, particularly in cybersecurity compliance. Master risk assessment techniques enable auditors to systematically identify, analyze, and prioritize potential organizational vulnerabilities.
The internal audit risk assessment process typically involves several critical stages:
Identification: Mapping potential risk areas across technological, operational, and strategic domains
Quantification: Evaluating the potential financial and operational impact of identified risks
Prioritization: Ranking risks based on likelihood and potential severity
Mitigation Strategy: Developing targeted approaches to address and minimize high-priority risks
Continuous Monitoring: Implementing ongoing assessment mechanisms to track risk evolution
Successful risk assessment demands a holistic approach that transcends traditional compliance checklists. Auditors must develop a dynamic understanding of an organization’s unique risk landscape, considering interconnected factors such as technological infrastructure, regulatory environment, organizational culture, and emerging threat landscapes.

Modern risk assessment requires sophisticated analytical capabilities that blend technical expertise with strategic thinking. Internal auditors must leverage advanced analytical tools, maintain deep technological knowledge, and cultivate a proactive mindset that anticipates potential security vulnerabilities before they can be exploited.
Pro tip: Develop a comprehensive risk scoring methodology that weights both quantitative metrics and qualitative insights to create a more nuanced risk assessment framework.
Governance and Strategic Oversight in Security
Cybersecurity governance represents a critical organizational imperative that extends far beyond traditional technical controls. Cybersecurity governance expectations have dramatically evolved, requiring comprehensive strategic oversight that integrates risk management across multiple organizational levels.
Key components of effective cybersecurity governance include:
Board-Level Accountability: Ensuring senior leadership actively engages with cybersecurity strategy
Risk Management Integration: Embedding cybersecurity considerations into enterprise-wide risk frameworks
Transparent Reporting: Developing robust mechanisms for communicating cybersecurity risks and mitigation strategies
Continuous Monitoring: Implementing dynamic assessment processes to track emerging technological threats
Strategic Investment: Allocating resources strategically to address evolving cybersecurity challenges
Successful governance requires breaking down traditional silos between technical and strategic functions. Internal auditors must act as critical bridge-builders, translating complex technological risks into meaningful business insights that resonate with executive leadership and board members.
Modern cybersecurity governance demands a proactive and holistic approach. Organizations must develop adaptive frameworks that can rapidly respond to emerging threats, integrate cutting-edge technological capabilities, and maintain a strategic perspective that balances risk mitigation with organizational innovation and growth.
Pro tip: Create a cross-functional cybersecurity governance committee that includes representatives from IT, legal, risk management, and executive leadership to ensure comprehensive strategic oversight.
Regulatory Requirements and Legal Mandates
Cybersecurity compliance represents a complex landscape of evolving legal requirements that demand sophisticated understanding from internal auditors. Cybersecurity standards and guidelines provide critical frameworks for organizations navigating increasingly complex regulatory environments.
Key regulatory requirements for cybersecurity compliance encompass multiple critical domains:
Federal Statutes: Comprehensive legal mandates governing data protection and security
Industry-Specific Regulations: Targeted requirements for sectors like healthcare, finance, and government
State-Level Cybersecurity Laws: Complementary regulations addressing regional security concerns
International Data Protection Standards: Global compliance requirements like GDPR
Incident Reporting Mandates: Legal obligations for disclosing security breaches
Internal auditors must develop a nuanced understanding of these regulatory landscapes, recognizing that compliance is not merely a checklist exercise but a strategic imperative. The legal mandates extend beyond technical controls, requiring organizations to demonstrate proactive risk management, comprehensive documentation, and robust incident response capabilities.
Navigating this complex regulatory environment demands continuous learning and adaptive strategies. Internal audit teams must maintain deep expertise across multiple regulatory frameworks, translating complex legal requirements into actionable organizational strategies that protect both technological infrastructure and business interests.
Pro tip: Develop a dynamic regulatory tracking system that continuously monitors changes in cybersecurity legislation across federal, state, and industry-specific domains.
Common Challenges and Errors in Cyber Audits
Cyber audits represent a complex landscape fraught with potential pitfalls that can compromise organizational security and compliance effectiveness. Cybersecurity best practices highlight the critical need for comprehensive and strategic audit approaches that address systemic vulnerabilities.
Common challenges and critical errors in cyber audits include:
Incomplete Asset Inventories: Failing to maintain accurate and comprehensive technology asset tracking
Inadequate Patch Management: Overlooking critical software and system updates
Superficial Risk Assessments: Conducting cursory evaluations without deep technological understanding
Inconsistent Policy Enforcement: Lacking uniform implementation of security protocols
Poor Incident Response Preparation: Neglecting to develop robust breach response mechanisms
Successful cyber audits demand more than technical competence; they require a holistic understanding of organizational risk landscapes. Auditors must transcend traditional compliance checklists, developing adaptive strategies that anticipate emerging technological threats and organizational vulnerabilities.
The following table illustrates the business impact of overcoming common cyber audit challenges:
Challenge Area | Consequence if Unaddressed | Business Benefit if Resolved |
Asset Inventories | Untracked vulnerabilities | Complete risk visibility |
Patch Management | Increased breach risk | Reduced attack surface |
Risk Assessments | Missed security gaps | Targeted risk mitigation |
Policy Enforcement | Inconsistent defense | Standardized security posture |
Incident Response | Prolonged recovery | Faster, coordinated response |
Modern cyber audit effectiveness hinges on continuous learning and proactive risk management. Internal audit teams must cultivate a dynamic approach that integrates technological expertise, strategic thinking, and deep organizational context to identify and mitigate potential security weaknesses before they can be exploited.
Pro tip: Implement a quarterly cross-functional audit review process that includes perspectives from IT, security, legal, and executive leadership to enhance comprehensive risk assessment.
Strengthen Your Internal Audit Role in Cybersecurity Compliance Today
Facing the complex challenges of cybersecurity compliance requires more than theoretical knowledge. As the article highlights, internal auditors must expertly navigate risk assessment, governance, regulatory mandates, and evolving cybersecurity frameworks such as NIST and ISO 27001. These critical responsibilities demand up-to-date skills and strategic insight to identify vulnerabilities and translate technical findings into actionable business solutions.
Elevate your expertise with tailored professional education and training from Compliance Seminars. Our comprehensive offerings including live webinars, in-person seminars, and CPE courses help you master internal audit standards, cybersecurity frameworks, and risk management strategies effectively. Start transforming your audit function with practical knowledge delivered by industry experts. Act now to secure your role as a proactive defender of organizational cybersecurity. Visit Compliance Seminars and explore our Continuing Professional Education courses designed specifically for auditors and compliance professionals.
Frequently Asked Questions
What is the role of internal audit in cybersecurity compliance?
Internal audit plays a critical role in cybersecurity compliance by systematically evaluating and enhancing an organization’s digital security posture, identifying vulnerabilities, ensuring regulatory alignment, and validating the effectiveness of security controls.
How do internal auditors assess cybersecurity risks?
Internal auditors assess cybersecurity risks through a multi-stage risk assessment process that includes identifying potential risk areas, quantifying their impact, prioritizing risks based on likelihood and severity, and developing mitigation strategies to address high-priority risks.
What cybersecurity frameworks are commonly used by internal auditors?
Commonly used cybersecurity frameworks by internal auditors include the NIST Cybersecurity Framework, ISO 27001, SOC 2, COBIT, and the CISA Critical Infrastructure Cybersecurity Framework. These frameworks help auditors evaluate digital security risks effectively.
What are some common challenges faced during cybersecurity audits?
Common challenges during cybersecurity audits include incomplete asset inventories, inadequate patch management, superficial risk assessments, inconsistent policy enforcement, and poor incident response preparation. Addressing these challenges is crucial for effective cybersecurity compliance.
Recommended
Comments